- Aircrack No File To Crack Specified Key
- Aircrack No File To Crack Specified 64-bit
- Aircrack No File To Crack Specified Server
Wi-Fi Crack allows you to crack any wireless network with WEP security. Powered by AirCrack-NG, the popular, cross-platform, wireless security cracking command-line tool, Wi-Fi Crack takes you step-by-step through the process of cracking the security of a WEP-based wireless network using a beautiful OS X graphical user interface. No file to crack specified. 'aircrack-ng -help' for help. Quitting aircrack-ng. So what do i do? (FYI I'm running a Raspberry Pi 2 with a Ralink Tech, Corp. RT5370 USB Wifi dongle with the latest release of the ARM Kali OS) Thanks in advance! It's probable that Gerix is freezing because the VM does not have enough resources to open the.cap file with aircrack. If you have 2.5 million IVs, the capture file is probably huge. This also slows down cracking. I second the suggestion to split your.cap file. Also try using '-ivs' with airodump-ng to only capture initialization vectors.
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK key cracking program.
Aircrack No File To Crack Specified Key
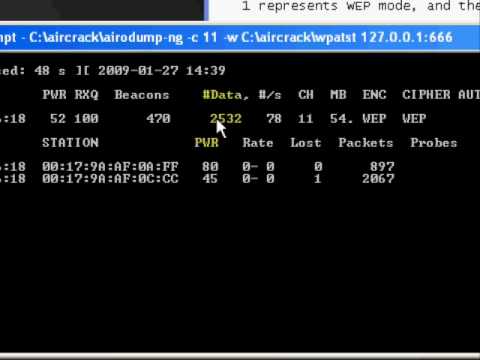
Aircrack-ng can recover the WEP key once enough encrypted packets have been captured with airodump-ng. This part of the aircrack-ng suite determines the WEP key using two fundamental methods. The first method is via the PTW approach (Pyshkin, Tews, Weinmann). The default cracking method is PTW. This is done in two phases. In the first phase, aircrack-ng only uses ARP packets. If the key is not found, then it uses all the packets in the capture. Please remember that not all packets can be used for the PTW method. This Tutorial: Packets Supported for the PTW Attack page provides details. An important limitation is that the PTW attack currently can only crack 40 and 104 bit WEP keys. The main advantage of the PTW approach is that very few data packets are required to crack the WEP key.
The other, older method is the FMS/KoreK method. The FMS/KoreK method incorporates various statistical attacks to discover the WEP key and uses these in combination with brute forcing. It requires more packets than PTW, but on the other hand is able to recover the passphrase when PTW sometimes fail.
Additionally, the program offers a dictionary method for determining the WEP key.
Aircrack No File To Crack Specified 64-bit
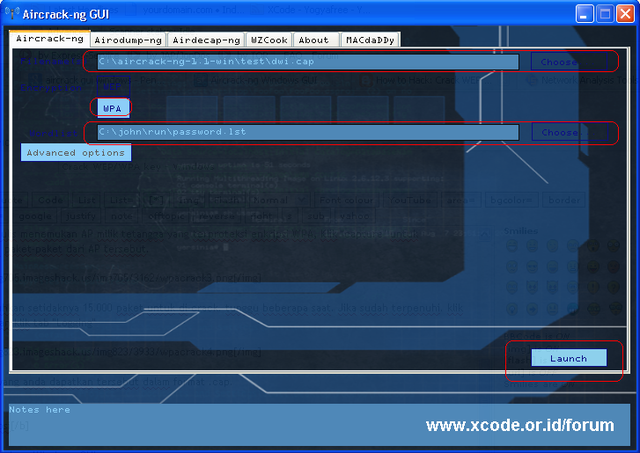
For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used. A “four-way handshake” is required as input. For WPA handshakes, a full handshake is composed of four packets. However, aircrack-ng is able to work successfully with just 2 packets. EAPOL packets (2 and 3) or packets (3 and 4) are considered a full handshake.

Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK key cracking program.
Aircrack No File To Crack Specified Key
Aircrack-ng can recover the WEP key once enough encrypted packets have been captured with airodump-ng. This part of the aircrack-ng suite determines the WEP key using two fundamental methods. The first method is via the PTW approach (Pyshkin, Tews, Weinmann). The default cracking method is PTW. This is done in two phases. In the first phase, aircrack-ng only uses ARP packets. If the key is not found, then it uses all the packets in the capture. Please remember that not all packets can be used for the PTW method. This Tutorial: Packets Supported for the PTW Attack page provides details. An important limitation is that the PTW attack currently can only crack 40 and 104 bit WEP keys. The main advantage of the PTW approach is that very few data packets are required to crack the WEP key.
The other, older method is the FMS/KoreK method. The FMS/KoreK method incorporates various statistical attacks to discover the WEP key and uses these in combination with brute forcing. It requires more packets than PTW, but on the other hand is able to recover the passphrase when PTW sometimes fail.
Additionally, the program offers a dictionary method for determining the WEP key.
Aircrack No File To Crack Specified 64-bit
For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used. A “four-way handshake” is required as input. For WPA handshakes, a full handshake is composed of four packets. However, aircrack-ng is able to work successfully with just 2 packets. EAPOL packets (2 and 3) or packets (3 and 4) are considered a full handshake.
Aircrack No File To Crack Specified Server
SSE2, AVX, AVX2, and AVX512 support is included to dramatically speed up WPA/WPA2 key processing. With the exception of AVX512, all other instructions are built-in Aircrack-ng, and it will automatically select the fastest available for the CPU. For non-x86 CPUs, SIMD improvements are present as well.

